SIEM | XDR with integrated AI intelligence
Available in our secure data center or deployable on-premises
Security Platform - GDPR-ready solutions
Integrated SIEM + XDR Monitoring
Detect, prevent, and respond to threats in real time with behavioral analysis and automated protection.
Key Features:
Real-time log and threat detection
File integrity and system change alerts
Automated blocking of suspicious actions
Vulnerability scanning with CVE priorities
MITRE ATT&CK threat mapping
Cloud & container security monitoring
Custom dashboards, alerts & audit-ready logging
Real-time cybersecurity monitoring and rapid response — all managed from a secure, high-availability data center.
SIEM | Managed XDR Protection

Advanced XDR Monitoring Solutions
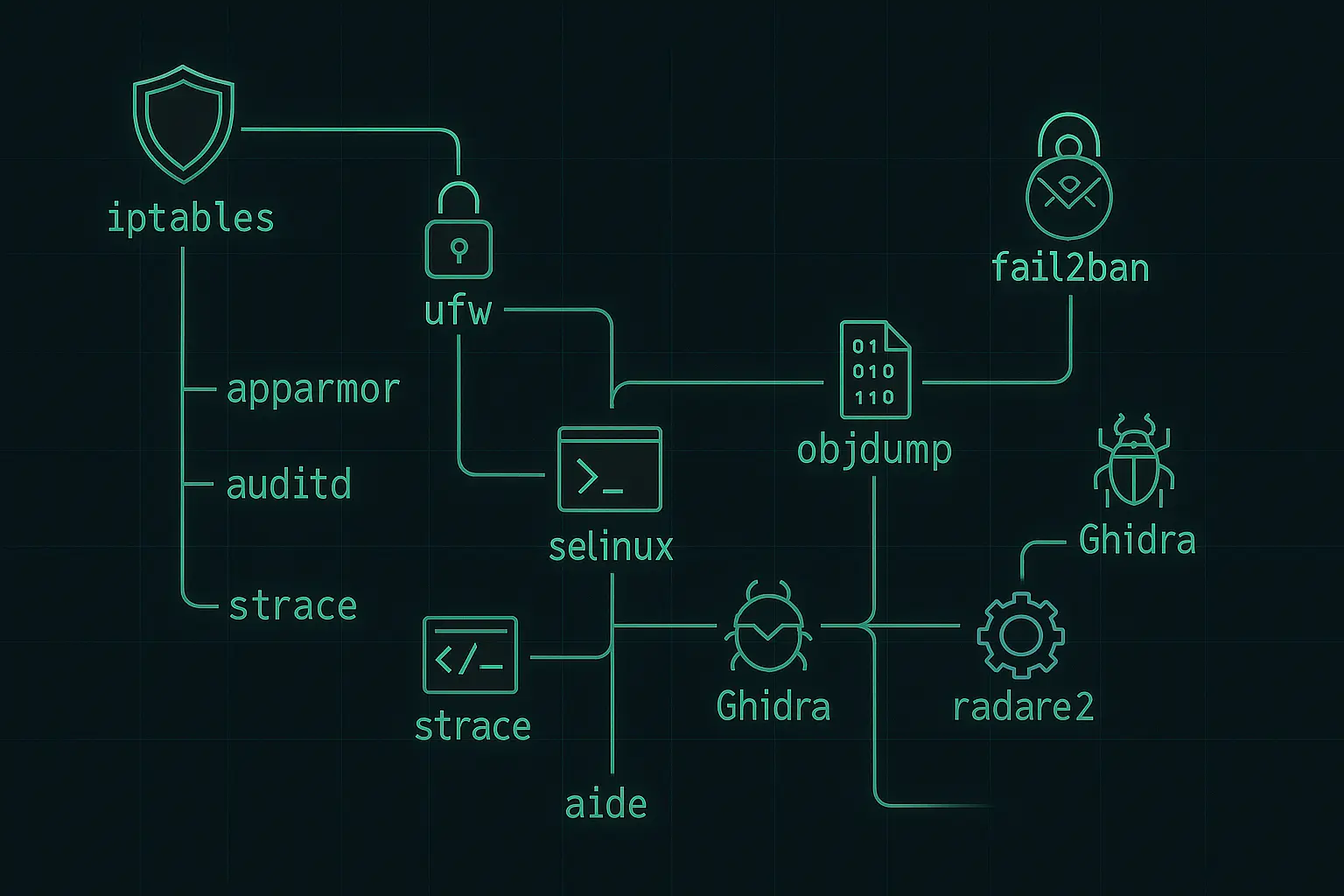
We monitor any computer or network in real time from our ISO 27001, ISO 9001, and NIS2-compliant security operations center to ensure it’s protected from cyberattacks. Our advanced SIEM | XDR (Extended Detection and Response) technology delivers continuous threat detection, rapid response, and deep visibility—keeping your systems secure, no matter where they are.
Real-time cybersecurity monitoring and rapid response — all managed from a secure, high-availability data center
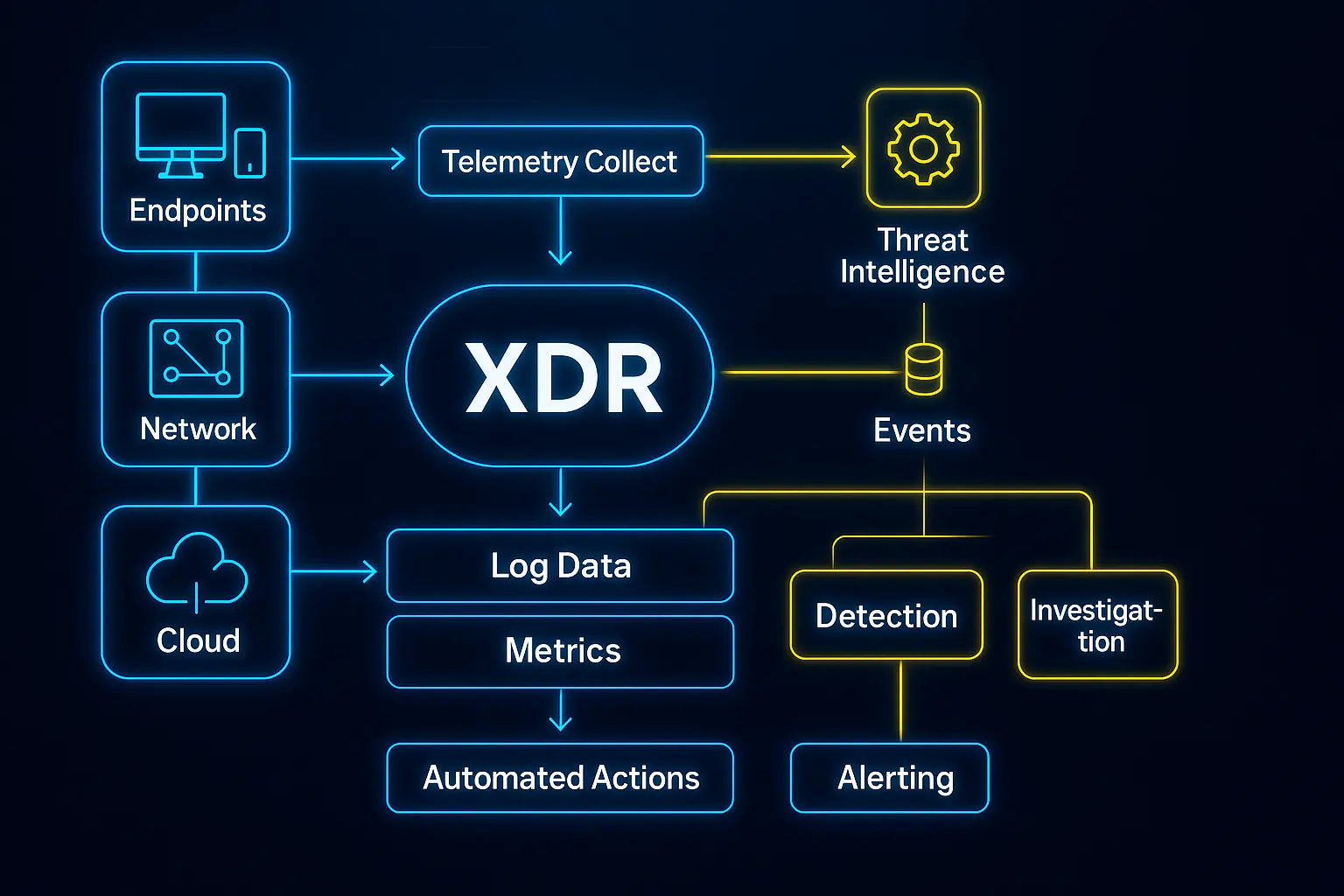
Gain full-spectrum threat visibility and protection through a unified security platform designed to monitor, detect, and respond to risks across endpoints, servers, networks, cloud, and containers. Key capabilities include:
Log Collection & Correlation
Collects and normalizes logs from endpoints, servers, network devices, and cloud services. Real-time correlation rules detect suspicious behavior, threat patterns, and compliance issues.
File Integrity Monitoring (FIM)
Monitors changes to system files, configuration files, and sensitive data—identifying unauthorized modifications, tampering, or potential ransomware activity.
Intrusion Detection System (IDS)
Analyzes system behavior, authentication attempts, and network traffic for known attack signatures, brute-force attacks, lateral movement, and privilege escalation attempts.
Intrusion Prevention System (IPS)
Supports automated containment actions such as blocking connections, disabling users, or isolating endpoints to prevent threat escalation.
Vulnerability Detection (CVE-Based)
Scans for known vulnerabilities by identifying software versions across systems and matching them against public CVE databases. Helps prioritize patching based on severity.
MITRE ATT&CK Mapping
Correlates detected tactics and techniques with the MITRE ATT&CK framework, giving analysts deeper context for adversary behavior and threat classification.
Security Configuration Assessment (SCA)
Performs system configuration checks based on industry best practices (e.g., CIS, NIST), detecting insecure settings and deviations from security baselines.
Cloud Security Monitoring
Monitors cloud workloads, APIs, audit logs, and identity activity to detect misconfigurations, policy violations, and unauthorized access attempts in real time.
Container & Orchestration Security
Monitors containers and orchestrators for abnormal behavior, vulnerability exposure, and runtime threats—ensuring security across DevOps environments.
Endpoint Threat Detection
Inspects endpoints for signs of malware, unauthorized access, and behavioral anomalies using agent-based monitoring.
Centralized Dashboards & Alerting
Visualizes threat data in real time via customizable dashboards and sends alerts based on rules, severity, and compliance status.
Automated Response Actions
Enables predefined responses such as killing malicious processes, blocking IPs, locking user accounts, or triggering external scripts based on threat intelligence and severity.
Secure Threat Monitoring Services — All Managed from Our Data Center
SIEM | XDR Threat Monitoring
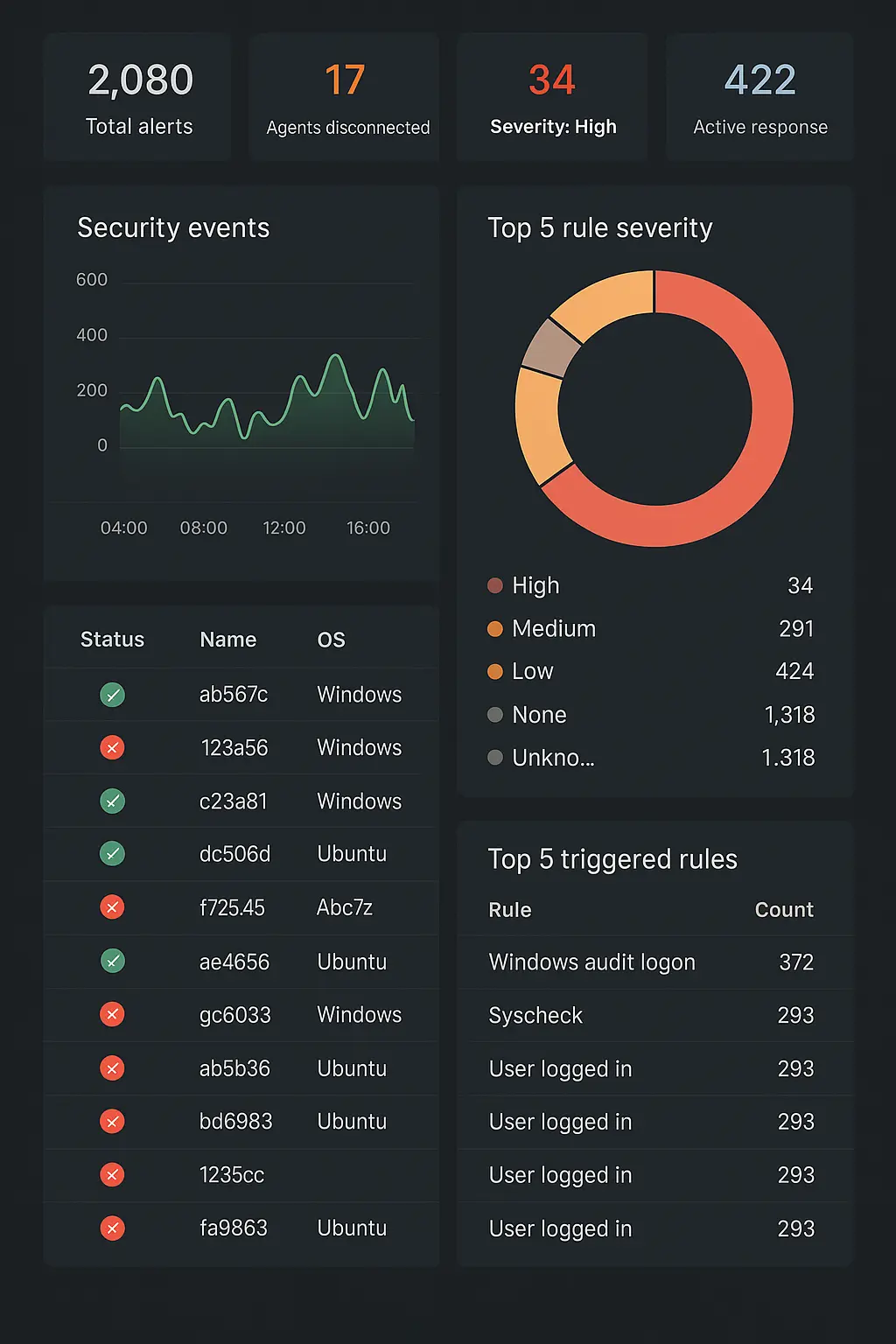
Real-time detection of threats, system anomalies, and unauthorized access attempts. We monitor logs, analyze behaviors, detect intrusions, and alert for vulnerabilities across your infrastructure — all managed from our secure data center.Secure VPN Access
Encrypted VPN connections for accessing private infrastructure, voice systems, from remote locations. Ensures confidentiality, data integrity, and reliable connectivity for remote workers or multi-location operations.
Security Event and Incident Monitoring (SIEM/XDR)
Protect your business with real-time monitoring for threats, vulnerabilities, and suspicious activity — powered by advanced analytics and secure data processing in our Finland data center.
We monitor your systems, logs, and endpoints for signs of intrusion or misuse and alert you instantly.
Simplify IT. Secure Everything. Communicate Freely
Integrating endpoints, network, and cloud data to deliver real-time threat detection, investigation, and automated response Better Bigger Faster